Threat Watch
Instantly assess your cybersecurity health with Threat Watch for vital insights on compromised accounts and devices.
Visit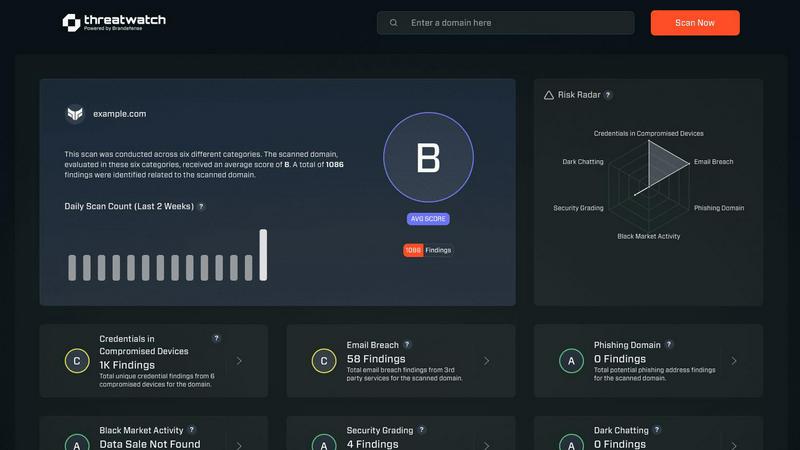
About Threat Watch
Threat Watch is a cutting-edge cybersecurity intelligence solution designed to empower organizations with vital insights into their cyber health. It meticulously analyzes an organization's assets, vulnerabilities, and exposures, delivering a comprehensive overview of security status. Ideal for businesses of all sizes, Threat Watch combines real-time insights with automated assessments to swiftly identify, prioritize, and mitigate risks. By evaluating critical security categories such as compromised credentials, breached accounts, phishing addresses, and dark web content, it equips users with essential information to take proactive measures against potential threats. The main value proposition lies in its ability to streamline the cybersecurity process, enabling organizations to respond more effectively to incidents and safeguard their digital assets.
Features of Threat Watch
Real-Time Insights
Threat Watch offers real-time insights that allow organizations to stay ahead of emerging threats. By continuously monitoring the cybersecurity landscape, it provides up-to-the-minute information that is crucial for making informed decisions and rapid responses to vulnerabilities.
Automated Assessments
With automated assessments, Threat Watch takes the manual effort out of security evaluations. This feature conducts regular scans of your organization's systems and networks, identifying vulnerabilities and exposures with minimal intervention, thus saving valuable time.
Comprehensive Security Evaluations
The software evaluates critical security categories to deliver a holistic view of an organization's cybersecurity posture. By assessing various elements such as compromised devices and breached accounts, users can understand their security landscape and address weaknesses effectively.
Dark Web Monitoring
Threat Watch includes dark web monitoring, which actively searches for compromised information related to your organization. By identifying leaked data or potential threats in the dark web, it enables businesses to take swift action to protect their sensitive information.
Use Cases of Threat Watch
Proactive Risk Management
Organizations can utilize Threat Watch to implement a proactive risk management strategy. By identifying vulnerabilities and exposures before they can be exploited, businesses can mitigate risks effectively and enhance their overall security posture.
Incident Response Preparation
Threat Watch prepares organizations for incident response by providing comprehensive insights into potential threats. This equips security teams with the knowledge they need to act quickly and efficiently during a cybersecurity incident, minimizing damage and recovery time.
Employee Training and Awareness
By leveraging the insights from Threat Watch, organizations can develop targeted training programs for employees. Educating staff on the latest phishing threats and compromised accounts helps build a culture of security awareness, reducing the likelihood of successful attacks.
Compliance and Regulatory Requirements
Threat Watch assists organizations in meeting compliance and regulatory requirements regarding data protection and cybersecurity. By providing detailed assessments and reports on security postures, it helps businesses demonstrate their commitment to safeguarding sensitive information and following industry standards.
Frequently Asked Questions
What types of organizations can benefit from Threat Watch?
Threat Watch is designed for organizations of all sizes, from small businesses to large corporations, that are looking to enhance their cybersecurity posture and protect their digital assets from evolving threats.
How does Threat Watch identify vulnerabilities?
Threat Watch identifies vulnerabilities through automated assessments that evaluate critical security categories. It continuously scans for compromised credentials, breached accounts, and other potential threats to provide a comprehensive overview of security health.
Can Threat Watch help with compliance requirements?
Yes, Threat Watch assists organizations in meeting compliance and regulatory requirements by providing detailed reports and assessments of their cybersecurity posture, ensuring that they adhere to industry standards for data protection.
Is there a trial version of Threat Watch available?
Yes, Threat Watch offers a free scan option for potential users. This allows organizations to experience the benefits of the solution and understand their cybersecurity health before committing to a subscription.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt simplifies contract management with secure templates, instant sharing, and automated reminders for seamless col...
aVenture
aVenture is an AI-powered platform for in-depth research on private companies, investors, and market trends.